Organizations are exploiting cloud services to accelerate business changes without the need for capital expenditure or lengthy procurement delays to obtain hardware. However, the dynamic nature of cloud services creates new security challenges that need a dynamic approach to governance and security controls.
In addition, the responsibilities for security and compliance are shared between the CSP (Cloud Service Providers) and the cloud customer and it is up to the customer to ensure that they use the cloud in a secure and compliant manner. On top of that, each cloud service provides its own proprietary tools for security.
How can an organization be sure that it is using cloud services securely and in a way that meets its compliance obligations and its appetite for risk?
Shared Responsibility
While major CSPs (Cloud Service Providers) go to great lengths to secure the services that they provide, it is up to the cloud service customers to secure how they use these services. The responsibility for security and compliance is shared between the cloud customer and the CSP. The customer does not manage or control the underlying cloud infrastructure but is responsible for managing everything above the service provided. The customer also remains responsible for compliance with laws and regulations governing the processing of their data.
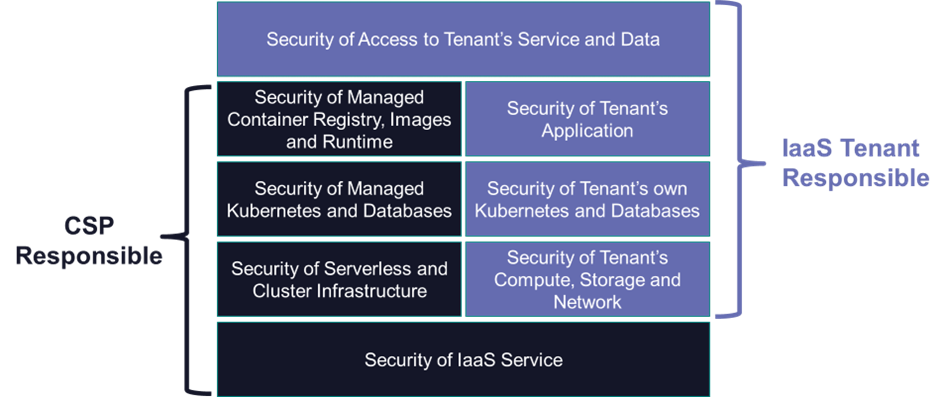
The basics of security hygiene are the same for both cloud and non-cloud. However, cloud and virtualized environments are very dynamic with resources being created and destroyed in milliseconds. Static detective controls are not appropriate in this dynamic environment. A policy-based approach is needed to prevent misconfigurations and vulnerabilities before they can be deployed rather than to detect them afterward. These policies are sometimes referred to as guardrails that stop mistakes before they create a risk.
Ad Hoc Approach
Cyber hygiene is a set of routines that implement best practices intended to keep systems, data, and users secure against cyber-attacks, data breaches, and data loss. These are the same for cloud services as for other forms of IT delivery. These are documented in numerous security frameworks and best practices and cover areas such as:
- Asset management – which needs an inventory – hard to maintain for the transient virtual resources.
- Identity management – which must also include the entitlements of the virtual resources.
- Vulnerability management – which must ensure that known vulnerabilities must be removed from virtual resources before they become live.
- Network security management – of the virtual in-cloud network as well as the connection to the cloud.
- Data protection – controlling what data is held in which locations and how this data is protected against theft and unauthorized access.
- Monitoring to ensure that the risks are managed and that obligations under laws and regulations are met.
However, each cloud has its own tools that support these processes, and these are all different. This has led to an ad hoc approach to security and compliance on the multi-cloud environment now found in most organizations.
Alphabet Soup
In response to these challenges, there is now a wide range of solutions on the market intended to help secure the way in which cloud services are used. While these tools are aligned with the security threats and risks that are relevant to the cloud they are often not integrated. To add to the confusion they are now referred to using yet another set of acronyms including:
- CAASM (Cyber Asset Attack Surface Management) - is an emerging technology focused on presenting a unified view of cyber assets to help prevent and manage attacks.
- CIEM (Cloud Infrastructure Entitlement Management) – provides controls over the entitlements possessed by virtual resources.
- CNAPP (Cloud Native Application Protection Platform) – provides capabilities to view and manage security controls for cloud accounts and workloads integrated into the cloud DevOps workflow.
- CSPM (Cloud Security Posture Management) - providing visibility of security and compliance posture.
- CWPP (Cloud Workload Protection Platform) – provides controls at the microservices instance/container level.
- CXDR (Cloud Extended Threat Detection and Response) – covering cloud threat detection and response.
- DSPM (Data Security Posture Management) – provides visibility into sensitive data, where it is located, and who has access.
- KSPM (Kubernetes Security Posture Management) – discover and fix security and compliance issues within the various Kubernetes components.
- SASE (Secure Access Service Edge) – provides network-based access controls to cloud services.
Cloud Security Platform
What is needed is a consistent cloud security platform that covers all the required capabilities for the customer to secure their use of cloud services. Some CNAPP solutions currently offered provide a platform that integrates several of the above capabilities for IaaS that were previously offered as standalone products. A key success factor for a cloud security platform is the ability of the tools to work in unison across environments, architectural layers, and, ideally, 3rd party integrations providing the additional context needed to achieve robust cloud security.
Attend Cyberevolution in Frankfurt, November 14-16, 2023, to navigate your way through the cloud security alphabet soup.